WordPress plugins are the lifeblood of many websites, offering essential functionalities that enhance user experience and site management. However, their widespread use also makes them a prime target for cyberattacks. This article delves into the story of how we were able to swiftly detect and neutralise a dangerous WordPress plugin exploit that threatened to compromise a client’s website.
Introduction
In the WordPress ecosystem, plugins are both a blessing and a potential curse. While they add invaluable features to websites, they can also introduce significant security risks if not properly managed or if they contain vulnerabilities. Plugin-related security issues are alarmingly common, and they can lead to severe consequences, including data breaches, site defacement, or even complete site takeovers.
Recently, one of our clients, a well-established media platform, faced a severe security threat due to a compromised WordPress plugin. The client’s website, with its vast audience and critical content, was a prime target for attackers. What followed was a demonstration of capability to manage and resolve such crises efficiently.
The Discovery
The plugin breach was first detected by our advanced security monitoring systems, which noticed unusual activity on the client’s website.
If left unchecked, the exploit could have allowed attackers to gain unauthorised access to the website, potentially leading to data theft, content manipulation, and a significant disruption of services. The stakes were high—any prolonged downtime or data compromise could severely impact the client’s reputation and business operations.
Our Rapid Response
Upon detecting the suspicious activity, our security team immediately took action to mitigate the threat. The first step was to isolate the website to prevent the exploit from spreading and causing further damage. The team quickly placed the website in a secure environment, ensuring that the malicious activity was contained.
The speed of the response was crucial. In security breaches, every second counts, and the ability to act swiftly not only prevented potential data loss but also minimised downtime for the client’s website. The real-time defence mechanisms played a pivotal role in keeping the situation under control.
To set the scene on the impact of Security Breaches and that even a big corporation can become a victim of it, here is a quick statistic on the biggest data breaches to date.
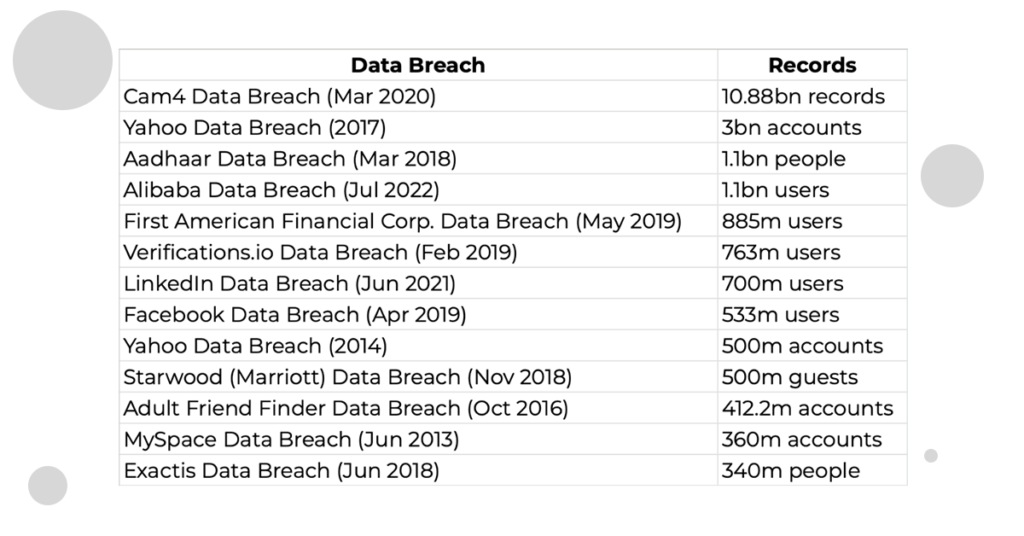
Most significant cases of data breach worldwide as of January 2024 (in millions), by number of compromised data records and individuals impacted, Statista, https://www.statista.com/statistics/290525/cyber-crime-biggest-online-data-breaches-worldwide/
Investigation and Analysis
With the immediate threat contained, our experts began a thorough investigation to identify the source of the breach. Through detailed analysis, they pinpointed the compromised plugin—a widely used plugin that, unbeknownst to many users, contained a critical vulnerability.
The exploit involved a remote code execution (RCE) vulnerability, which allowed attackers to inject and execute malicious code on the server. This type of exploit is particularly dangerous as it can give attackers full control over the website, enabling them to access sensitive data, modify content, and even disrupt the entire site.
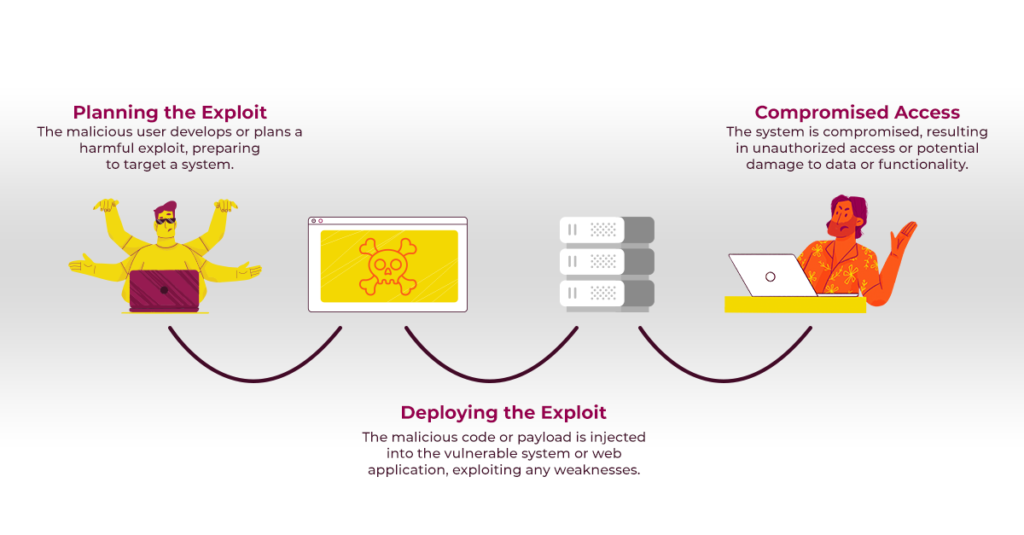
The Fix
Once the compromised plugin was identified, we took swift action to remove the threat. The steps involved:
- Plugin Deactivation and Removal: The team immediately deactivated the compromised plugin and removed all its associated files from the server to eliminate any potential backdoors left by the attackers.
- Malware Scanning and Removal: The website underwent a comprehensive malware scan to ensure that no malicious code remained hidden within the site’s files or database. Any detected threats were promptly neutralised.
- Patch Implementation: We collaborate as much as possible with the plugin’s developers to patch the vulnerability. The developers released a security update, and we ensured that it was applied to all affected websites hosted on their platform.
- Security Hardening: We went beyond simply patching the issue. They implemented additional security measures, including stronger firewall rules, enhanced user access controls, and automated plugin updates, to prevent similar incidents in the future.
Recovery and Reinforcement
After the immediate threat was removed, we focused on ensuring that the website was fully secure and operational. We conducted a series of post-incident checks to verify that no residual threats were present. This included a detailed review of server logs, user access records, and content integrity.
To bolster the website’s defenses, we had implemented additional security measures tailored to the client’s needs. These included regular security audits, real-time monitoring, and automated backup solutions to ensure that the website could be quickly restored in case of any future incidents.

Long-term Impact
The successful resolution of this plugin breach not only restored the client’s website to full functionality but also significantly improved its overall security posture, which was done swiftly, and the issue was resolved in mere minutes after the security team had been alerted. The incident highlighted the importance of proactive security measures and the value of having a responsive and knowledgeable hosting provider.

Lessons Learned
This incident serves as a valuable reminder of the critical importance of plugin management and security. Here are some actionable lessons for website owners:
- Regularly Update Plugins: Ensure that all plugins are kept up to date with the latest security patches. Outdated plugins are a common entry point for attackers.
- Choose Trusted Plugins: Only use plugins from reputable developers who have a proven track record of maintaining and updating their products.
- Conduct Regular Security Audits: Periodic security checks can help identify vulnerabilities before they are exploited.
- Monitor Website Activity: Implement real-time monitoring to detect and respond to suspicious activity as soon as it occurs.
- Collaborate with Your Hosting Provider: Partner with a hosting provider like us, that prioritises security and has the expertise to handle incidents swiftly and effectively.
By following these best practices, you can significantly reduce the risk of plugin-related breaches and keep your WordPress site secure. Our experience in this case underscores the importance of vigilance, quick action, and expert intervention in maintaining the integrity of your online presence.